Phishing Simulations Made Easy. Using Microsoft Defender for Office 365 to Protect Your Organisation
A guide for running phishing simulations, training employees, and configure anti-phishing policies with Microsoft Defender for Office 365
When it comes to safeguarding your organisation against email-based threats, Microsoft Defender for Office 365 offers robust tools designed to address today’s complex security challenges. However, unlocking its full potential depends on choosing the right licensing plan. So let’s take a look at the different options below:
Don’t forget to check out my YouTube channel Control Alt Delete Tech Bits >here< where I have a video covering Attack Simulator, Training Campaigns and Threat Policies.
Microsoft Defender for Office 365 Plan 1:
A solid entry point that includes essential features like anti-phishing, anti-spam, and malware protection.
Ideal for smaller organisations or those starting their journey towards enhanced email security.
Microsoft Defender for Office 365 Plan 2:
Everything in Plan 1, plus advanced features such as:
Attack Simulator and Training
Automated Investigation and Response (AIR)
Threat Analytics
Tailored for larger organisations or those requiring a more comprehensive approach to threat management.
Microsoft 365 E5:
Includes Plan 2 capabilities within the broader E5 license, offering extensive tools for enterprise-grade security and compliance.
Add-On Licenses: Organisations using Microsoft 365 E1 or E3 can purchase Defender for Office 365 as an add-on, enabling advanced security features without upgrading their entire plan.
The Microsoft Defender for Office 365 Attack Simulator is a hands-on tool designed to help IT administrators evaluate their organisation’s ability to withstand phishing attacks. Phishing remains a prevalent attack method, often targeting unsuspecting employees. This feature allows organisations to simulate real-world attacks and provide employees with the knowledge they need to spot suspicious activity. Here’s a closer look at how it works.
A quick rundown of the Phishing Simulator
Access the Portal: Head over to https://security.microsoft.com and log in with your admin credentials.
Navigate to the Attack Simulator: Once inside the portal, go to Email & Collaboration, then select Attack Simulation Training.
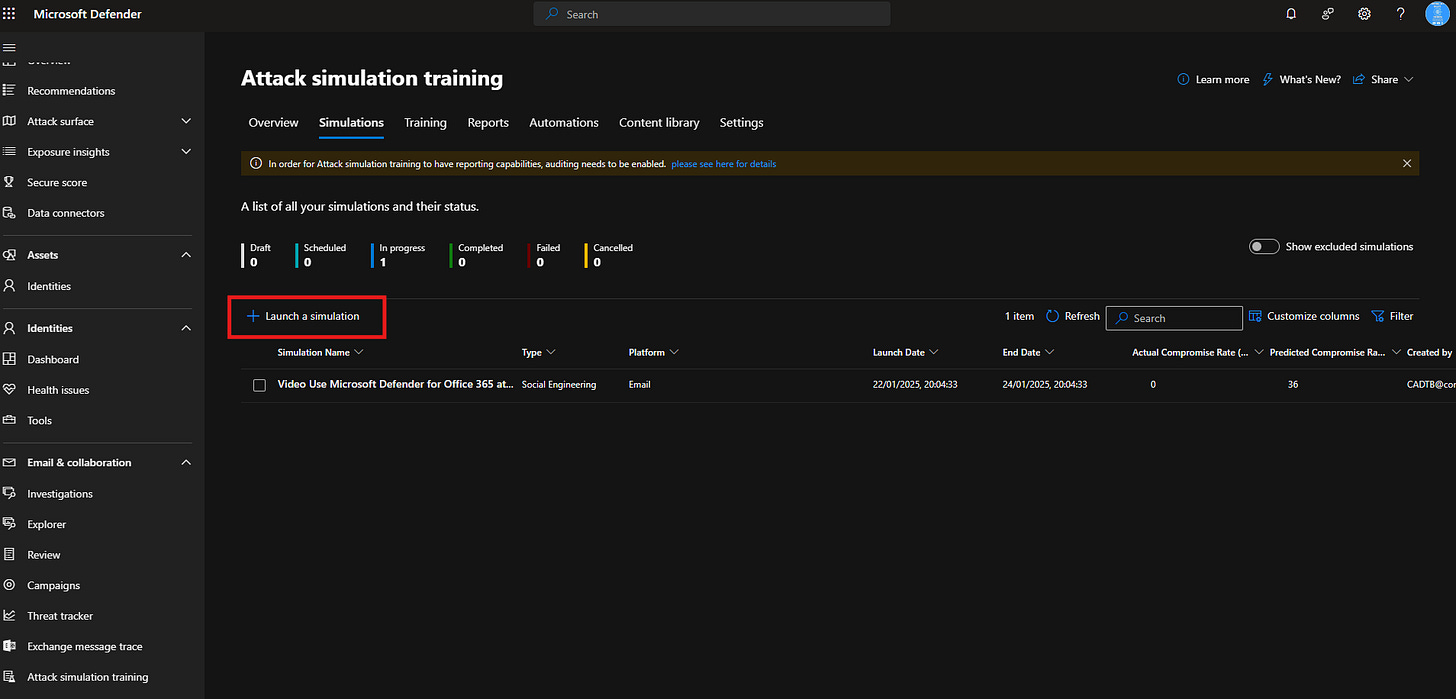
Launch Your Simulation:
Click Simulations and then Launch a Simulation.
Pick a phishing template—prebuilt options include credential harvesting emails and malicious attachments. Want to get creative? Build a custom template tailored to your organisation’s needs.
Choose Your Target Audience: Assign the simulation to specific users or groups.
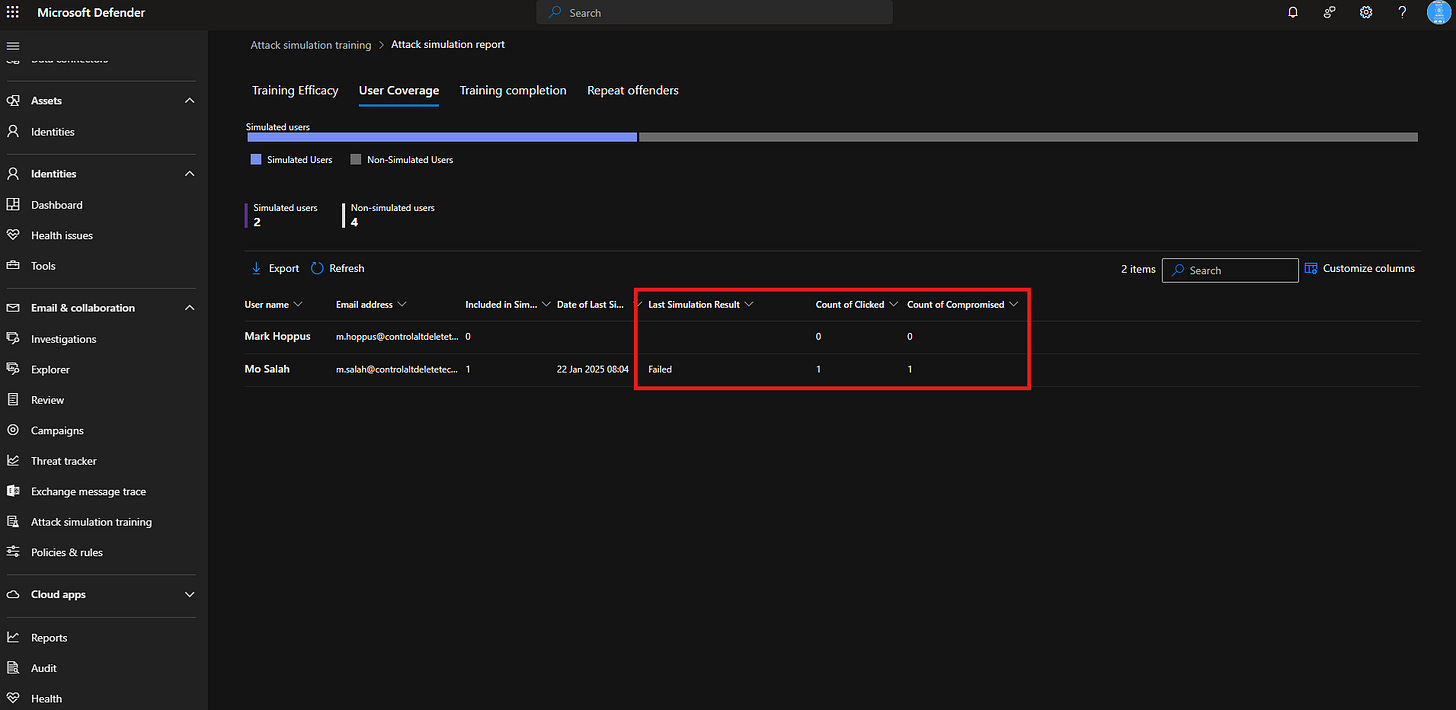
Monitor the Results: After the simulation is live, track how users interact with it. Metrics like email opens, link clicks, and credential submissions provide insights into vulnerabilities.
Assign Follow-Up Training: Employees who fall for the simulation can be automatically assigned phishing awareness training. This ensures lessons are learned and mistakes aren’t repeated.
Training Campaigns
Simulations are just one piece of the puzzle. For long-term success, organisations need to reinforce awareness with ongoing education. Microsoft Defender for Office 365 makes this simple with training campaigns that:
Deliver interactive modules, including videos and quizzes, tailored to employees who failed simulations.
Track completion rates and provide administrators with detailed insights into employee progress.
Allow customisation to align with specific organisational policies or compliance requirements.
By combining simulations with effective training, you’re building a workforce that’s prepared to spot and avoid phishing attacks.
Threat Policies
Prevention is always better than reaction, and anti-phishing threat policies in Microsoft Defender for Office 365 are designed to stop attacks before they reach your users. Let’s take a look at some key configurations:
Impersonation Protection:
Guard against attackers spoofing executives, trusted domains, or internal email accounts.
Set up specific rules to flag or block emails attempting impersonation.
Spoof Intelligence:
Enable AI-driven detection to identify and block emails that use domain spoofing tactics.
Quarantine and Review Options:
Define actions for detected phishing emails. You can choose to quarantine, delete, or flag them for user awareness.
Mailbox Intelligence:
Use machine learning to detect unusual patterns in email delivery and interaction.
These policies not only reduce risk but also give administrators greater control over how email-based threats are managed.
The Value of Proactive Defence
Phishing accounts for over 90% of cyberattacks, making it a critical focus for organisations to tackle. Using phishing simulations, training campaigns, and anti-phishing policies together helps shift your approach from reactive to proactive. By pinpointing at-risk users, providing them with targeted education, and implementing automated protections, you strengthen your organisation’s overall security and reduce the likelihood of successful attacks
Turning Awareness into Action
Security isn’t a one-time effort; it’s an ongoing process. Microsoft Defender for Office 365 equips organisations with the tools they need to stay ahead of evolving threats. From running phishing simulations to educating users and deploying advanced anti-phishing policies, it provides a comprehensive approach to email security.